#
[CTF] Solving Verilog CTF Onchain (Simple)
#
Introduction
Source code of the challenge: https://github.com/Verilog-Solutions/CTF-2022-wMaticV2
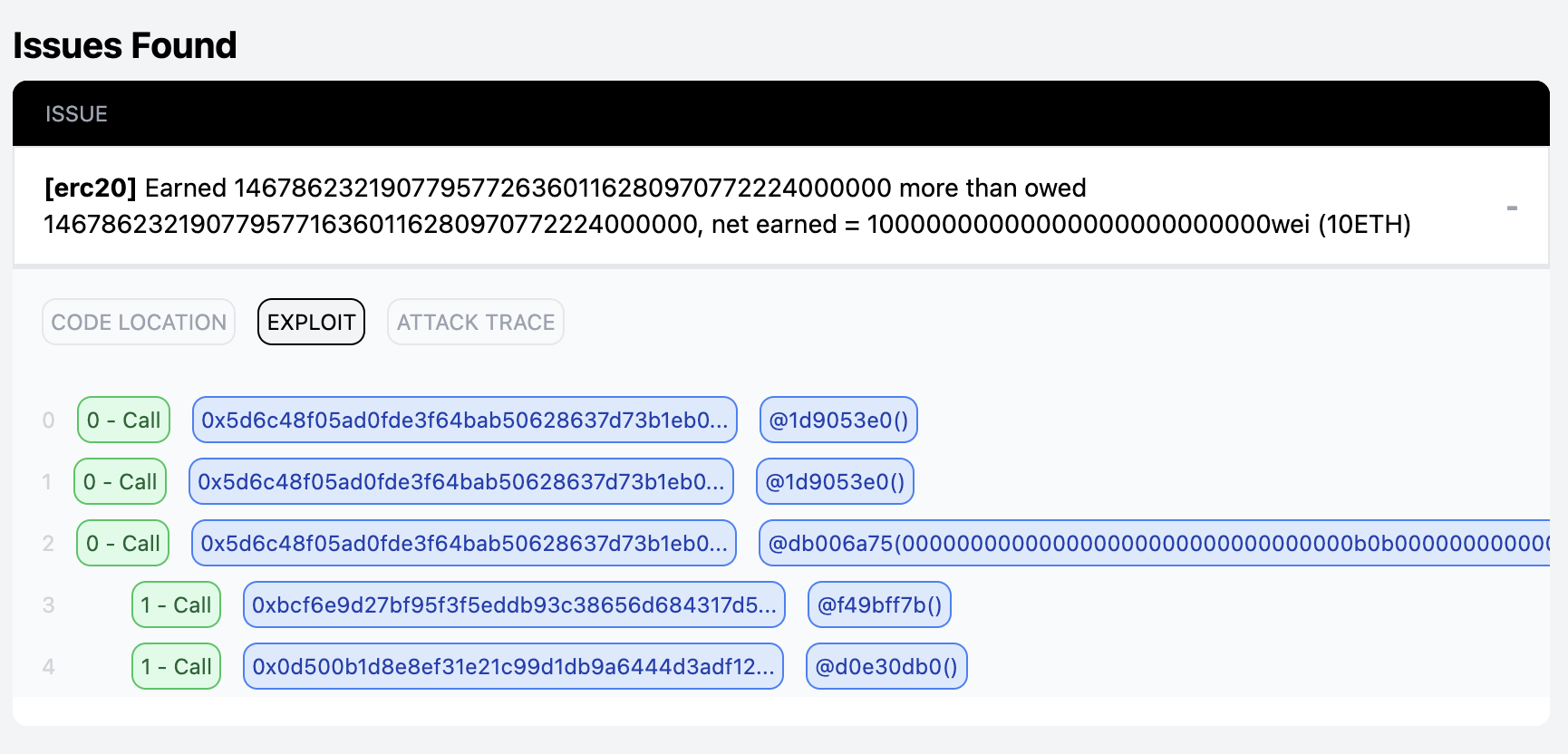
The project consists of a buggy WMATICv2 token contract containing a function redeem allowing reentrancy attack. Additionally, there is a Bounty.sol contract, which rewards the first person who successfully calls its getBounty function.
There are two trackers of total supply of WMATICv2 token and our goal is to successfully call getBounty, which requires these two trackers to be significantly deviated.
#
Using Blaz to Solve
Here are the contracts we are interested:
WMATICV2:
- 0x5d6c48f05ad0fde3f64bab50628637d73b1eb0bb
- https://polygonscan.com/address/0x5d6c48f05ad0fde3f64bab50628637d73b1eb0bb
Bounty:
- 0xbcf6e9d27bf95f3f5eddb93c38656d684317d5b4
- https://polygonscan.com/address/0xbcf6e9d27bf95f3f5eddb93c38656d684317d5b4
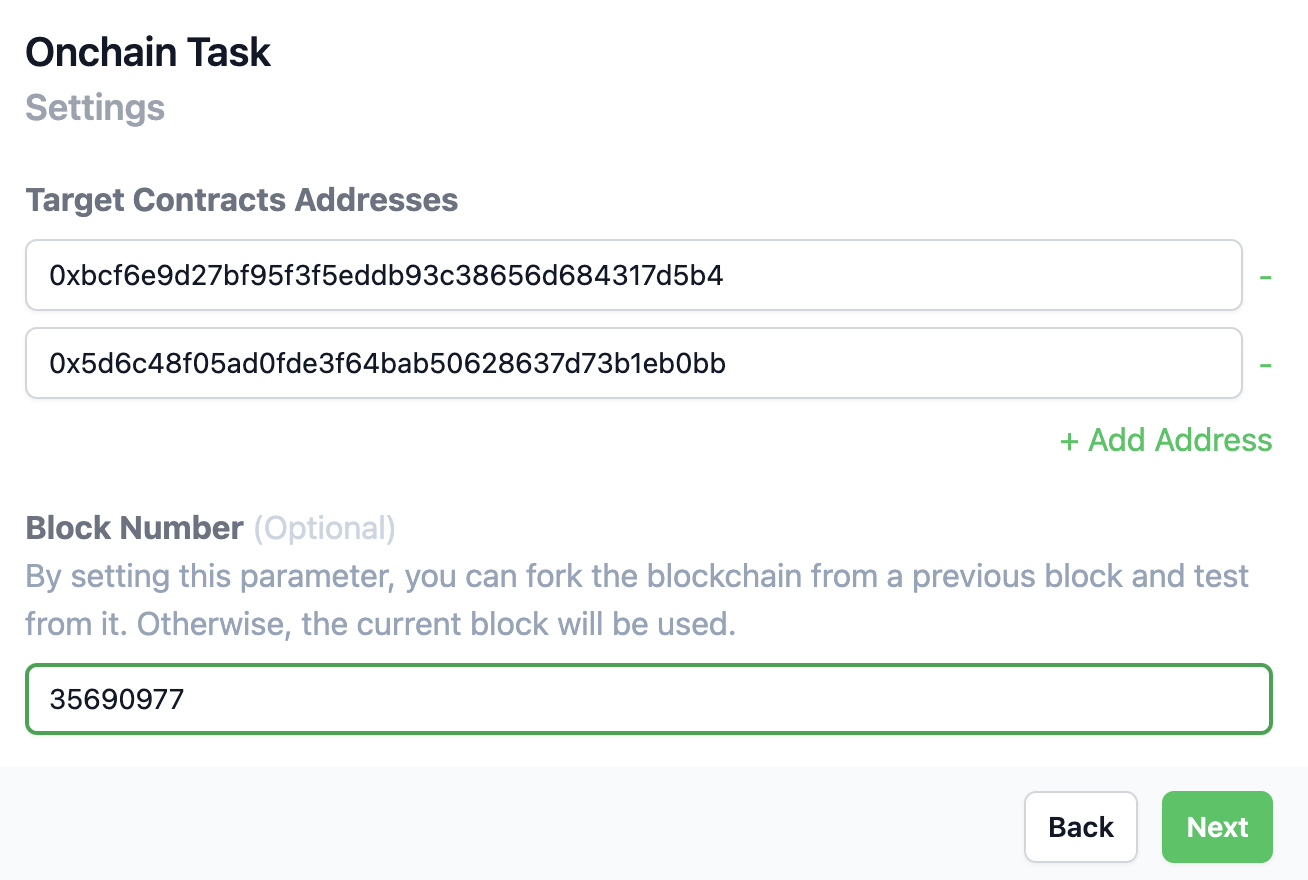
The contracts are exploitable before block number 35690977. We'll fork the chain at block number 35690976 and let Blaz find the exploit for us.
#
Step 1
Select Polygon and click Next. Then, put the contract address and block number as follows:
#
Step 2
Select all Common Vulnerabilities and submit the job. You'll find results in a few minutes.